Top 10 Best Ethical Hacking Tools In India In 2023.

Finding security holes in a system, application, or organization’s infrastructure that a hacker could exploit to harm someone or something with some tools is referred to as Ethical Hacking. By legally breaking into the systems and searching for ways to get inside and take things out, they use this method to stop cyberattacks and security breaches.
To gain Access and test the organization’s network and strategies, an ethical hacker mimicked a malicious attacker’s actions and thought processes. They operate in this manner.
The same five steps are always used when someone attempts to hack into a network or computer system. Exploiting vulnerabilities, maintaining steady Access to the system, and then erasing one’s footprints are the first steps in ethical hacking.
The five stages of ethical hacking are as follows:
1. Initial reconnaissance
Reconnaissance, also referred to as the process’s information gathering phase or footprint is the first step in the ethical hacking methodology. To gather as much knowledge as you can is the aim of this phase. The attacker gathers all the information he requires about the target before launching an attack.
Passwords, crucial employee information, and other information will likely be included in the data. Additionally, HTTPTrack and search engines like Maltego can be used by an attacker to gather information about a person. These tools can download an entire website and gather data on a person.
Ethical hacking heavily relies on reconnaissance. It aids in identifying potential attacks and the likelihood that those attacks will compromise the organization’s computer systems.
With this approach, you can gather information from sources like:
- People can use two different types of services: TCP and UDP.
- The network host can connect to the network using particular IP addresses.
- You leave a trail, for instance, when you ethically hack.
There are two categories:
Active: Using Nmap tools to scan the target’s network and gather information from the target, this footprinting technique collects data from the target.
Passive: The second type of footprinting involves learning details about a target without touching them. Social media accounts, public websites, and more are sources from which attackers or ethical hackers can obtain the report.
2. Scannable
The second step in the hacking process is for the hacker to look for ways to obtain the target’s information. They search for things like IP addresses, user names, and passwords. In this stage of ethical hacking, you search for quick and simple methods to enter the network and look for data.
In the scanning phase, a wide variety of tools, such as dialers, port scanners, network mappers, sweepers, and vulnerability scanners, are required to scan data and records. The ethical hacking method includes four different ways to scan for malware.
A person searches for flaws and vulnerabilities in a target during vulnerability scanning, looking for ways to take advantage of those flaws. Automated tools like Netsparker, OpenVAS, Nmap, and others are used to complete it.

Listen for open TCP and UDP ports, active services, and live systems on the host you want to check using port scanners, dialers, and other data-gathering tools and software. These individuals, also known as attackers or penetration testers, use this scanning to look for openings in a company’s system.
By using this practice, find out what devices are on a network and how to connect to a network. For example, it might be an organizational network, similar to one in a business, where all employee systems are interconnected. By identifying holes and opening doors, network scanning can increase the security of an organization’s network.
3. Obtaining entrance
When a hacker uses any means necessary to gain Access to the target’s systems, applications, or networks, they have advanced to the next hacking stage. A computer or other machine can be accessed by an attacker using a variety of tools and techniques.
This is when hackers attempt to access the system and carry out actions like downloading harmful software or applications, stealing crucial data, gaining unauthorized Access, demanding a ransom, and more. Social engineering is one of the most popular ways to access a computer out of the many possible methods.
Potential entry points can be secured, all systems and applications can be password-protected, and the network can be secured with a firewall thanks to ethical hackers or penetration testers. They can determine which employee is most likely to be hacked by cybercriminals by sending phony social engineering emails to the staff members.
4. Keeping Access
As soon as an attacker has Access to the target computer, they can enter the system and will stop at nothing to maintain that Access. At this point, the hacker either carries out DDoS attacks against the system or steals the entire database.
Two tools that can enter an unsafe computer and steal crucial data are a backdoor and a Trojan. While the user is unaware of it, the attacker keeps their unauthorized Access during this phase until they have finished their malicious work.
In order to prevent system hacking or use, they can use this phase to scan the entire organization’s infrastructure for malicious activities and their source.
5. Making Headway
Because no one wants to get caught by the law, the final stage of ethical hacking asks hackers to make sure they don’t get caught. In order to prevent the attackers from being apprehended, this step ensures that they leave no traces or signs that could be used to identify them.
This is crucial because ethical hackers need to maintain a connection to the system without being detected by the incident response or forensics teams. This includes modifying, erasing, or corrupting registry keys or logs.
The attacker engages in other activities as well. Additionally, they remove or delete software, applications, and folders, or they make sure that the altered files can be located and restored to their original state.
Use these techniques to erase your ethical hacking footprints:
- Reverse HTTP Shells are possible, and clearing the cache and history will remove all traces of your online activity.
- You can send messages over the Internet using ICMP (Internet Control Message Protocol) tunnels.
- Ethical hackers or penetration testers can use these five steps of the CEH hacking methodology to find and fix flaws, identify potential entry points for cyberattacks, and safeguard their organizations from security breaches.
- You can obtain an ethical hacking certification to learn more about analyzing and enhancing security procedures and network infrastructure. The Ethical Hacking course from the EC-Certified Council teaches students how to access a company using hacking tools and technologies legally.
- It is ethical to hack into a computer or network to check for hidden threats. The phrase “ethical hacking” is often used interchangeably with the phrases “penetration testing,” “intrusion testing,” and “red teaming.”
- Hacking is the act of identifying and using security holes to gain Access to a computer system for illegal activities like data theft and privacy violations. An “Ethical hacker” is a hacker who engages in hacking activities.
Six distinct categories of hackers:
- Ethical hacking (White Hat)
- Cracker
- Grey Hat
- The Script Kiddies
- Hacktivist
- Phreaker
A security professional who only uses hacking skills for protective purposes is an ethical hacker. Ethical hackers use their knowledge to find security flaws, note them, and suggest fixes.
Companies that provide online services or are connected to the internet must undergo penetration testing by ethical hackers. Penetration testing is another name for ethical hacking. It can be carried out manually or through an automated program.
Professionals in the field of information security, ethical hackers. These criminals attempt attacks against a computer system, network, or application to find security flaws and then offer suggestions or advice on strengthening security.
The most common hacking languages are PHP, SQL, Python, Ruby, Bash, Perl, C, C++, Java, VBScript, Visual Basic, C Sharp, JavaScript, and HTML.
A few hacking certifications are as follows:
- CEH
- GIAC
- OSCP
- CREST
Top 10 Best Ethical Hacking Tools In India In 2023
1. Acunetix
Acunetix is an automated ethical hacking tool that identifies and reports over 4500 online application vulnerabilities, including all SQL Injection and XSS variants.
Since the Acunetix crawler supports HTML5, JavaScript, and single-page applications, authenticated apps can be audited with it. In addition, it prioritizes risks based on data, integrates the scanner’s findings into other tools and platforms, and incorporates cutting-edge Vulnerability Management components into its core.
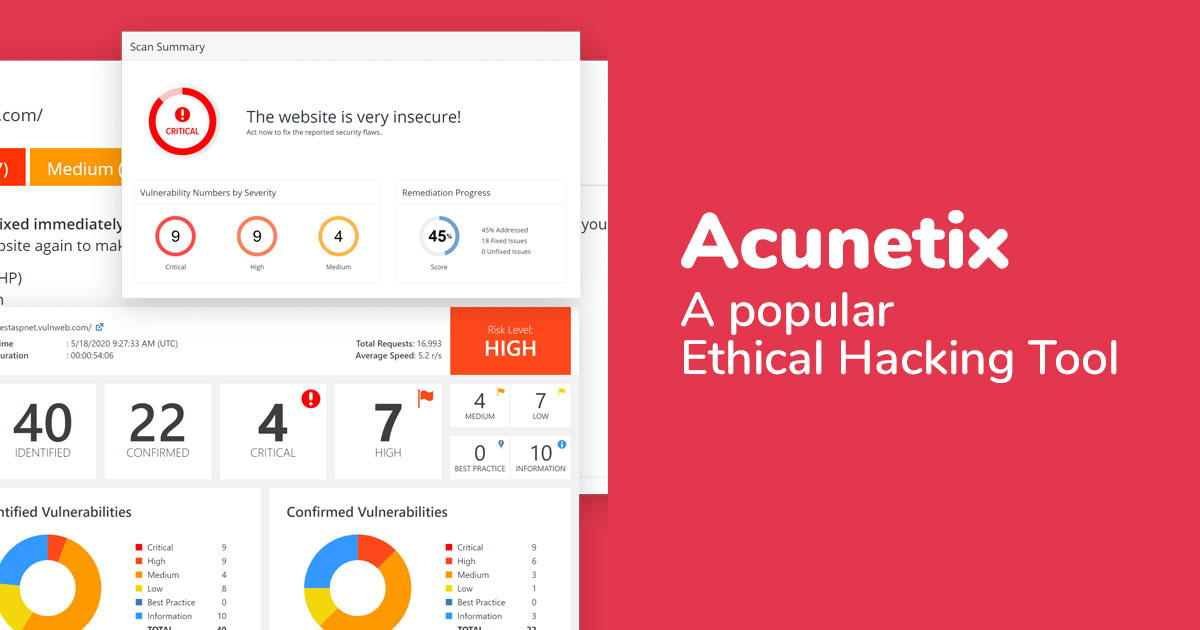
Key characteristics are:
- Unified perspective.
- Scanner results integration with other platforms and tools.
- Putting risks in order based on data.
2. Netsparker
An ethical hacker can find security flaws like SQL Injection and Cross-site Scripting in web APIs and online applications using Netsparker.
After a scan is finished, it is unnecessary to manually verify the vulnerabilities found because Netsparker checks each one individually, demonstrating that they are real and not false positives. You can use this product with either software or internet service.
![NET - Reverse Engineering] Netsparker 4.9.1.15947 - RDot: White Hat Security Community](http://i.imgur.com/HASJvoJ.png)
Features consist of:
- Available as a Windows program or online service
- Uniquely verifies vulnerabilities to demonstrate that they are genuine and not false positives.
- Eliminates the need for manual verification, saving time.
3. Intruder
A fully automated scanner known as an intruder finds and fixes cyber security flaws in your digital estate. These kinds of ethical hacking tools should be a part of your arsenal.
Thanks to Intruder’s 9,000 security tests, enterprises of all sizes can now perform enterprise-level vulnerability scanning. Its security assessments include checking for configuration errors, missing updates, and common web application issues like SQL injection and cross-site scripting.
A vulnerability management tool called an intruder was created by seasoned security professionals to free you up to focus on what really matters. Since it scans your systems for the most recent vulnerabilities and prioritizes results based on context, you don’t need to worry about it. Intruder supports a number of popular cloud services, including Jira, Slack, and Jira.

Features comprised:
- Identifies missing patches, configuration errors, and typical cross-site scripting and SQL Injection problems with web apps
- Integrates with major cloud providers like Jira, Slack, and
- Prioritizes outcomes according to context
- Proactive system scanning for the most recent vulnerabilities
4. Nmap
Nmap is a network exploration tool, a security scanner, and a port scanner. Since it is open-source software, downloading and using it are both free.
It works across platforms. This tool is used to monitor host and service uptime, network inventory, and service upgrade schedules. Both small and large networks can use it. Additionally, it provides binary distributions for Linux, OS X, and Windows.
Features:
- Capabilities for data transferring, rerouting, and debugging are all present (Ncat).
- Results of scanning evaluating the value (Ndiff).
- A program for creating packets and evaluating responses (Nping).
- Results with Graphical User Interface Viewer (Nping).
When analyzing raw IP packets, the following can be done:
- Possible network resources to use.
- They offer their goods and services through these easily accessible hosts.
- Their operating system is referred to as OS.
- There are packet filters in use.
- And a plethora of other qualities.
- A network scanner’s paradise, in other words! It is quick as well as easy to use.
5. The Metasploit Framework
The open-source, free Metasploit Framework software is available. It costs money to use Metasploit Pro, though you can try it out for 14 days without paying anything. Contact the company for more details about prices.
You can find pen testing software here. You can create and execute code against a remote computer using Metasploit. It works across platforms.

Features:
- Knowing if there are any security flaws is useful.
- Makes it possible to perform penetration testing more successfully.
- Helps with IDS signature creation.
- It is possible to create your own security-testing tools.
- This software works best for creating anti-forensic and evasion programs.
- The first autonomous retail store in India is Watasale Store.
6. Aircrack-Ng
This service is provided without cost. Tools are available from Aircrack-ng to evaluate Wi-Fi security.
All of them are command-line programs. It is primarily concerned with watching, harassing, testing, and circumventing Wi-Fi security measures. Numerous operating systems, including Linux, Windows, OS X, Free BSD, NetBSD, OpenBSD, and Solaris 2, are compatible with it.
Features:
- Iarcrack-ng can target replay, de-authentication, bogus access points, and more.
- Data can be saved as plain text files.
- Using this tool, Wi-Fi cards and drivers can be tested.
- It uses PTW, FMS, and dictionary attacks to crack WEP keys.
- It uses dictionary attacks to crack WPA2-PSK.
- The best controller for any wireless network interface is a specialty.
7. Wireshark
This service is provided at no cost. Using the packet analyzer in Wireshark, many protocols can be examined. It works across platforms. The output can be exported to file formats in XML, PostScript, CSV, and Plaintext. It can apply color rules to packet lists to expedite analysis. This image demonstrates the packet capture process.

Features:
- Gzip files can be instantly decompressed.
- It can be used to decrypt a variety of protocols, including IPsec, ISAKMP, SSL/TLS, and many more.
- It comes with a built-in camera for both live and offline analysis.
- The GUI and TTY modes of TShark allow you to examine the gathered network data.
- Ideal for decoding and analyzing data packets is a specialty.
8. OpenVAS
The OpenVAS Open Vulnerability Assessment Scanner’s features include unauthenticated and authenticated testing as well as speed optimization for extensive scans.
In addition to a number of high- and low-level internet and industrial protocols, it has a robust internal programming language. The scanner’s extensive history of upgrades and updates over time allows it to perform vulnerability testing.
9. SQLMap
This automated tool can take over database servers and find and exploit SQL injection issues.
It is a piece of strong detecting software that is free. It works with many databases, including PostgreSQL, Oracle, and MySQL. This SQL injection tool supports stack queries, out-of-band queries, error-based queries, UNION queries, and boolean blind queries.
SQLMap can download and upload any file, run any command with the expected results, look up specific database names, and do a lot more things. Utilizing this tool will make connecting to the database simpler.
Features of SQLMap include:
- Robust detection system.
- Allows the execution of any command.
- Includes PostgreSQL, Oracle, MySQL, and more.
10. NetStumbler
Discovering wireless networks can be done by using NetStumbler. Windows is compatible with it. There are three different ways to identify wireless LANs: 802.11b, 802.11a, and g. GPS support is built into MiniStumbler, a scaled-down version of the software for portable Windows CE operating systems.
The NetStumbler tool can be used to verify network configurations, locate areas with patchy WLAN coverage, detect wireless interference, and locate unauthorized access points.

Uses for the NetStumbler ethical hacking program include:
- The AP (Access Point) network configuration to be identified
- Identifying the interference’s causes
- Determining the signal strength received
- Discovering unapproved access points
What are hacking software and tools?
Hacking is the process of gaining unauthorized Access to data for the security measures of a computer system or network by using a variety of tools or technology in the form of computer programs and scripts.
The software and tools used by hackers to discover vulnerabilities in computer operating systems, a variety of web applications, servers, and networks are nothing more than computer programs or a sophisticated type of script created by developers.
These days, a lot of employers, particularly in the banking industry, use ethical hacking tools to protect their data from intruders. Hacking tools can be purchased or downloaded in open source (shareware or freeware) or commercial solutions. If someone wants to use such tools maliciously, they can also be downloaded from the browser.
Security experts use ethical hacking tools specifically to gain Access to computer systems in order to discover their vulnerabilities and strengthen their security. Security experts use hacking tools like packet sniffers, password crackers, port scanners, etc., to eavesdrop on network traffic, crack passwords, find open ports on computers, etc. Although there are many different hacking tools on the market, always keep in mind what they should be used for.
However, over the past few years, the field of network administration has experienced tremendous growth. Initially used only for network monitoring, it is now also capable of managing firewalls, intrusion detection systems (IDS), VPNs, anti-virus programs, and anti-spam filters.
Nmap (Network Mapper), Nessus, Nikto, Kismet, NetStumbler, Acunetix, Netsparker, and Intruder are some of the most well-known hacking tools on the market.
How Does a Hacking Software Work?
Here’s how to begin using any hacking software, whether it’s from the list above or somewhere else on the Internet:
- Install the preferred hacking program you like after downloading it.
- Once the software has been installed, run it.
- Choose and configure your hacking tool’s startup options.
- Examine the tool’s features and interface to become familiar with it.
- Use a preconfigured external browser to test the software.
- Use the hacking software to perform penetration testing or website scanning.
Is It Legal to Use Hacking Tools?
If you meet both of the following requirements, you are permitted to use hacking tools:
- You are employing the resources for lawful hacking.
- The target site that you intend to “attack” has given you written consent.

Why using Hacking Software is Important?
We frequently experience anxiety or paranoia when it comes to hacking software because we worry that it will harm our computer system. The reality, however, is so dissimilar that employers might require a professional expert to safeguard sensitive information regarding valuable company assets, hardware, and software systems from hackers. As a result, ethical hacking has become so essential and necessary that businesses have started hiring ethical hackers. The following are a few crucial characteristics of hacking software:
- In order to protect end users from threats, it offers both inside and outside security.
- By identifying and closing any gaps in the network security, it is used to test that security.
- Additionally, one can download open source ethical hacking software to protect their home network from threats.
- A vulnerability assessment can also be obtained to safeguard a network or system from outside threats.
- It is also used to audit the company’s security by confirming that the computer system is operating faultlessly.
Conclusion:
Companies employ ethical hackers to find and fix security holes in their computer and network infrastructure. EC-Council also offers the Certified Network Defense Architect credential (CNDA). This certification is only available to staff members of specific US government agencies, including some commercial government contractors, in accordance with DOD Directive 8570.01-M. A training facility that has both ANSI accreditation and GCHQ approval (GCT).

Employers now look for skilled and certified ethical hackers by enrolling in courses like the Certified Ethical Hacking Course to stop fraud and identity theft due to the growing Internet security threats. End users have consistently been the weakest points through which cybercriminals are able to breach even the most advanced defenses. In the recent past, a number of sizable companies have disclosed significant security breaches. Tools for ethical hacking assist businesses in finding potential gaps in internet security and preventing data breaches.
Information security experts who follow strict ethical rules are known as ethical hackers. Ethical Hacking (White Hat) Intruder is a vulnerability management hacking tool created by seasoned security professionals that helps you to concentrate on the things that really matter instead of stressing about the rest.
The network exploration program Nmap can be used to scan for ports, security threats, or both. With the help of the tool Metasploit, you can write code and execute it on a distant computer. AiRCrack can exploit WPA2-PSK or other security flaws by decrypting WEP keys using a variety of techniques, including FMS, PTW, and dictionary attacks. Use the tool Netstumbler to discover fresh wireless networks.
edited and proofread by nikita sharma






