Top Encryption Algorithms: What Is Data Encryption?
Top Encryption Algorithms: What Is Data Encryption?
If you are a PC user or a business owner, then secure data transfer may be one of the most important activities for you. Ignoring this activity can mean huge losses. However, it doesn’t matter whether you have anything in your personal or business account, it is important to keep what you have completely secure. Although many technology experts have unveiled many ways to keep data transfer secure, data encryption is considered to be one of the most common and easiest methods when it comes to security. Its use and complete knowledge about it are very important for a PC user. In addition, the data is thoroughly “scrambled” through encryption to keep it safe from any intruders. Most of the Bitcoin millionaires got their start in cryptocurrencies when they were young.

On the other hand, a format of data that is involved in data encryption as a translation, such that only a person interested in it can read it if they have the decryption key (secret key). In addition, the data is viewed and referred to as plaintext in its entirety, before encryption. Whereas, once the encryption is done, the data is known as ciphertext. Data encryption is usually performed intentionally to protect the confidentiality of information during the process of being transferred from one computer system to another or while it is being stored. Currently, the main goal of developing new encryption algorithms is to completely replace the old DES – data encryption standard – where computing systems and prior information play a very important role in securing security. On the other hand, if we talk about modern encryption tools, they come with privacy properties such as data authentication, data integrity, as well as non-revocation features.
Advanced Encryption Standard (AES)

Here if we talk about AES encryption, it is currently being used most popular and widely. The main reason for the development of AES, however, was due to the need for a replacement for DES, due to its lower computing power and smaller key size. Being the world’s most accepted encryption standard, the AES acronym seems to be popping up all over computer screens, especially concerning cyber security. Furthermore, approximately 3 block ciphers are constituted by the AES standard, where cryptographic keys are typically used to perform data encryption and decryption in each 128-bit block cipher. Here if we talk about encryption and decryption, usually the same key is used for both, so the same key is found with both the receiver and the sender.
IDEA Encryption Algorithm
The key size of which is close to 128 bytes and is largely seen as the best and most secure public standard. In hindsight, this protocol has been seen in the market for many years, where no attacks have been revealed to identify them despite many tests. Block ciphers usually operate on round blocks. It starts with only about fifty-two subkeys, each almost 16 bytes in length.
Blowfish Encryption Algorithm
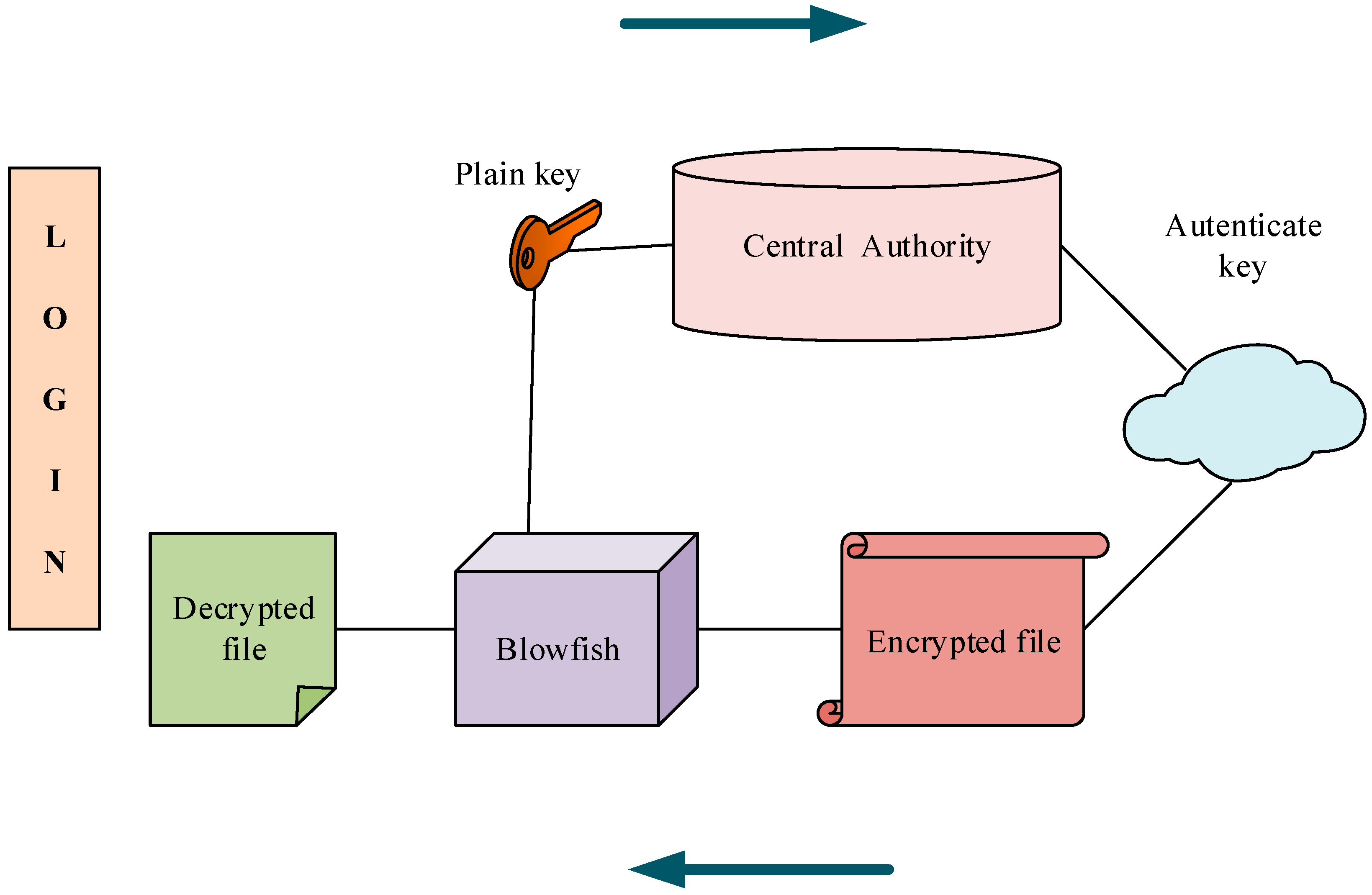
The Blowfish encryption algorithm was developed in 1993 as an alternative to the Data Encryption Standard (DES). So that it can be easily available to the user, it has been put forward in the form of a protocol by the developer. In a sense, it has emerged as an asymmetric type of encryption protocol. Its block size is close to 64-bit and if we talk about the size of the key, it is anywhere between 32 – 448 bits. There are about 18 subkeys, four S-boxes, and sixteen rounds. The Blowfish standard, also called a Feistel cipher, refers to the use of a single structure, usually for encrypting and decrypting data.







