Cyberattacks in India will take a new drastic turn in 2022

Cyberattacks in India will take a new turn in 2022
Cybercriminals took advantage of the new normal engulfing the world in 2021, targeting employees who worked from home, COVID vaccine research, and a myriad of other opportunistic cyberattacks to disrupt organizations’ supply chains and networks, further their geopolitical agenda, among other heinous actions.
The sophistication and scale of the attacks led to international headlines, and. Ransomware proved to be a significant disruption. Global cybercrime syndicates emerged for the first time out of the shadows in 2021.
As cybercriminals evolve their modus operandi in 2022, they will become increasingly sophisticated and modify their tactics, techniques, and procedures to outsmart cyber defenders effectively. The cyber defender will quickly realize that no surface is safe from the reach and influence of cybercriminals.
Cybercriminals are attracted to a kinetic cyberattacks.

According to trends analysis of cyber-attacks, we expect cyber-attacks to escalate beyond the current crop of non-violent or non-kinetic attacks into exploiting vulnerable systems and processes in 2021. Having the victims face real-life damage can serve two objectives:
1) Improve their willingness to negotiate, and
2) Increase their credibility amongst peers, further improve their ability to bring in significant financial gains, cause maximum reputational damage, and recruit affiliates.
Such attacks have occurred throughout history, with damage inflicted on water facilities, hospitals, transportation systems, and manufacturing plants, such as the infamous Stuxnet worm.
Increasing numbers of cyber-attacks will target PLCs, ICS devices, critical infrastructure, healthcare, and research organizations as cybercriminals seek to transcend the physical and cyber worlds. There will be actual physical damage and loss of lives due to geopolitical tensions, commercial competition, and socio-economic differences.
To build a robust security posture, security mechanisms and controls must be agile enough to keep up with the rapid evolution of external threats. In addition to protecting data, this will also save lives.
Cyberwar will become an everyday occurrence.
Targeting other nations will be accomplished primarily through cyber warfare this year. Increasing geopolitical tensions between major countries will surprise corporate entities and private actors.
Cybercriminals and threat actors turn to supply chain attacks for financial and geopolitical gains. Such attacks have become more common in semiconductors, energy, and pharmaceutical companies.
Cyberattacks will target critical infrastructure, leaving millions vulnerable.
Cyberassaults and espionage by state-sponsored threat actors and other organizations will continue against nations and organizations. Various partnerships will mushroom based on geopolitical needs and wants, resulting in a new power dynamic in the world.
Business entities and private actors will use cyber espionage to advance commercial interests. Cyberwarfare will no longer be the province of nation-states.
Ransomware attacks on mobile devices
Both cybercriminals and state-sponsored threat actors will continue to focus their efforts on mobile devices in 2022. An ideal spy bug is attached to a treasure chest of valuable information.
There is no mature and robust security system on mobile to detect and prevent phishing, C2 traffic, credential theft, and other attacks.
Voice call (vishing) phishing, phishing on messaging apps, and malicious apps on the app store are all on the rise.
A supply chain attack can target mobile device management platforms to get a foothold in an organization’s network.
In 2022, cybercriminals will target mobile devices and operating systems like Android and iOS to introduce malicious applications that exploit legitimate software to attack mobile devices and operating systems.

We cannot imagine life without our mobile phones, which have become indispensable. Cybercriminals will extort ransoms from mobile devices in 2022, knowing that many will succumb to extortion tactics and take over the devices.
Mobile users need to improve their cybersecurity knowledge and practice safe cyber habits, including setting secure passwords, becoming aware of emerging cyber threats like phishing campaigns and social engineering lures, and keeping an eye out for apps that cybercriminals target. Mobile security should not be neglected.
Considering that security breaches are increasing in both number and complexity, we suggest organizations reevaluate their current cybersecurity strategies. Enterprises need to adopt threat landscape management procedures to get visibility into emerging threats to take proactive measures to protect data and assets.
Beware! Attacks on cyberspace may reach a new level in 2022
- Hackers are embracing Attacks-as-a-Service
Cyberspace faces a year when sophisticated phishing, ransomware, and malware attacks will increase in sophistication, just as the physical world in 2022 began with an Omicron scare. Cyber-attacks-as-a-service are becoming increasingly popular. As hackers can just rent out or buy the skills they don’t possess, the bar has been lowered for them to launch sophisticated attacks.
The difficulty of tracing cryptographic transactions has also provided cybercriminals with fertile ground. Besides state-sponsored groups, cybercriminals may try to take advantage of investors with fraudulent rogue wallets in 2022. In an age when work and study are shifting from the office to the home and video-conferencing is replacing in-person business meetings, cybersecurity has assumed nightmare proportions. In addition, the issue is no longer just an enterprise problem; it has become a problem affecting everyone, from the general public to government agencies.
- Attacks using advanced technology
A new attack, Ransomware 2.0, emerged in 2021 that went beyond mere extortion to encrypting and deleting data and exporting. VPN credentials stolen from exploited remote machines have allowed attackers to access the target organization’s internal network, steal sensitive data, and perform ransomware attacks. Cybercriminals are using Cyber-Attack-as-a-Service tools, says Himanshu Dubey, Senior Director (Engineering) of Quick Heal’s Security Labs.
In a fascinating development, some attack groups are selling access to large botnets of infected machines throughout businesses; this lowers the entry barrier for hackers. Threat actors will increasingly target organizations on multiple fronts in multi-vector attacks, QuickHeal predicts.
Cyber-attackers claim to be resorting to aggressive extortion such as threatening employees, pressuring victims to pay, or threatening to publish or sell the data, according to Sunil Sharma, Managing Director (Sales) at Sophos (India and SAARC).
- Crises are exploited
Covid-19 has demonstrated how cybercriminals are willing to exploit crises like this to target critical infrastructure, such as healthcare and vaccination supply chains, says Barracuda Networks APAC Vice President James Forbes-May. According to IBM, data breaches in India are estimated to cost an average of *16.50 crores in 2021, and the amount is 17.85 per cent higher than the previous year. Loss or theft of records cost $5,900, up 6.85 per cent from 2020.
Indian sites targeted in cyberattacks in the past ten months

The Indian Parliament was informed that almost 26,000 websites were hacked in 10 months ending in October.
According to a written reply, the CERT-In network reported that, between 2018 and 2020 (up to October), there were 17,560 hacks, 24,768, 26,121, and 25,870 hacks, according to October) Rajeev Chandrasekhar, Minister of State for Electronics and IT.
Cybersecurity incidents in India are tracked and monitored by the Indian Computer Emergency Response Team (CERT-In).
According to a minister’s reply to the lower house, cyber-attacks are conducted from time to time on Indian cyberspace. Attackers compromise computer systems in other countries and use remote servers to hide the identity of the actual systems coming from which attacks are launched.
According to CERT-In’s analysis of the logs, computers associated with these attacks often come from as diverse a variety of countries as Algeria, Brazil, China, France, Germany, Hong Kong, Indonesia, Netherlands, North Korea, Pakistan, Russia, Serbia, South Korea, Taiwan, Thailand, Tunisia, Turkey, USA and Vietnam.
Moreover, he added that the government is fully aware of various cybersecurity threats, including cyberterrorism, and has taken multiple steps to enhance its cybersecurity posture and prevent attacks.
According to cybersecurity and digital privacy firm Kaspersky, cyber espionage-related security breaches involving India are among the top five targets of cyberattacks in the Asia Pacific region.
Kaspersky’s newest report titled Cyberthreats to Financial Organizations in 2022 contains these findings.
Kaspersky views the APAC region as one of the hottest targets for cyberattacks, mainly because digital technologies are rapidly advancing. At the same time, cybersecurity awareness is relatively low, and mitigation resources are limited.
Various reports on cybersecurity found India ranking among the top 5 targets of cyberattacks, with cyber espionage as a significant threat. Attacks like APTs (Advanced Persistent Threats) will increase in frequency to provide valuable business, geopolitical and military intelligence.
Kaspersky (South Asia) General Manager Dipesh Kaura said, “Some countries, such as India, are still targets of advanced Cybercrime. An elevated threat level is a consequence of its burgeoning economy and expected growth.
Investing in infrastructure and capabilities to improve cyber intelligence by improving predictions is the only proper response. Providing our clients with such services is a crucial offering of Kaspersky. It is commendable that India has recently taken decisive steps toward enhanced cyber threat vigilance.”
China and Pakistan round out the top five countries.
The APAC region is thus the epicentre of cyber conflict in India. According to Kaspersky’s findings, cyberattacks are also a significant threat to Singapore. India’s businesses with ties to Singaporean entities and presence in Singapore need to pay attention. The new NFT industry and cryptocurrencies will be affected by data breaches in Singapore.
“A proactive, concerted approach to preventing cyber-attacks can be very effective,” says Saurabh Sharma, Senior Security Researcher (GReAT), Kaspersky (APAC). Every business and institutional process that uses data must adopt this approach.”
Recently, cyberthreats and cyberattacks have risen sharply in the APAC region. Though digital technologies are widely adopted today, awareness levels and security infrastructure remain low, allowing such attackers to escape without being identified as the perpetrators of their crimes. It is only through updating cybersecurity infrastructure and upskilling personnel that cybercriminals will be brought to justice.
Cybersecurity in India in 2022: Trends to Watch
The hybrid work era’s more complicated IT requirements and any human or technical flaws will almost certainly continue to let cybercriminals take advantage of us in 2022. Increasing complexity means that threat actors will continue to exploit vulnerabilities that organizations cannot rectify, allowing them to advance their interests.
Due to the new distributed workforce and the increasing rate of cyberattacks in India, this trend continues. India is one of the top countries for cyberattacks during the pandemic. Indian organizations invest heavily in cyber security to protect themselves from threats, which will boost the market to USD 3.05 billion by 2022.
Cybercriminals will almost certainly continue to exploit human and technical flaws, as well as hybrid work’s increased IT requirements, through the year 2022. The following trends will affect security in India in the coming year.
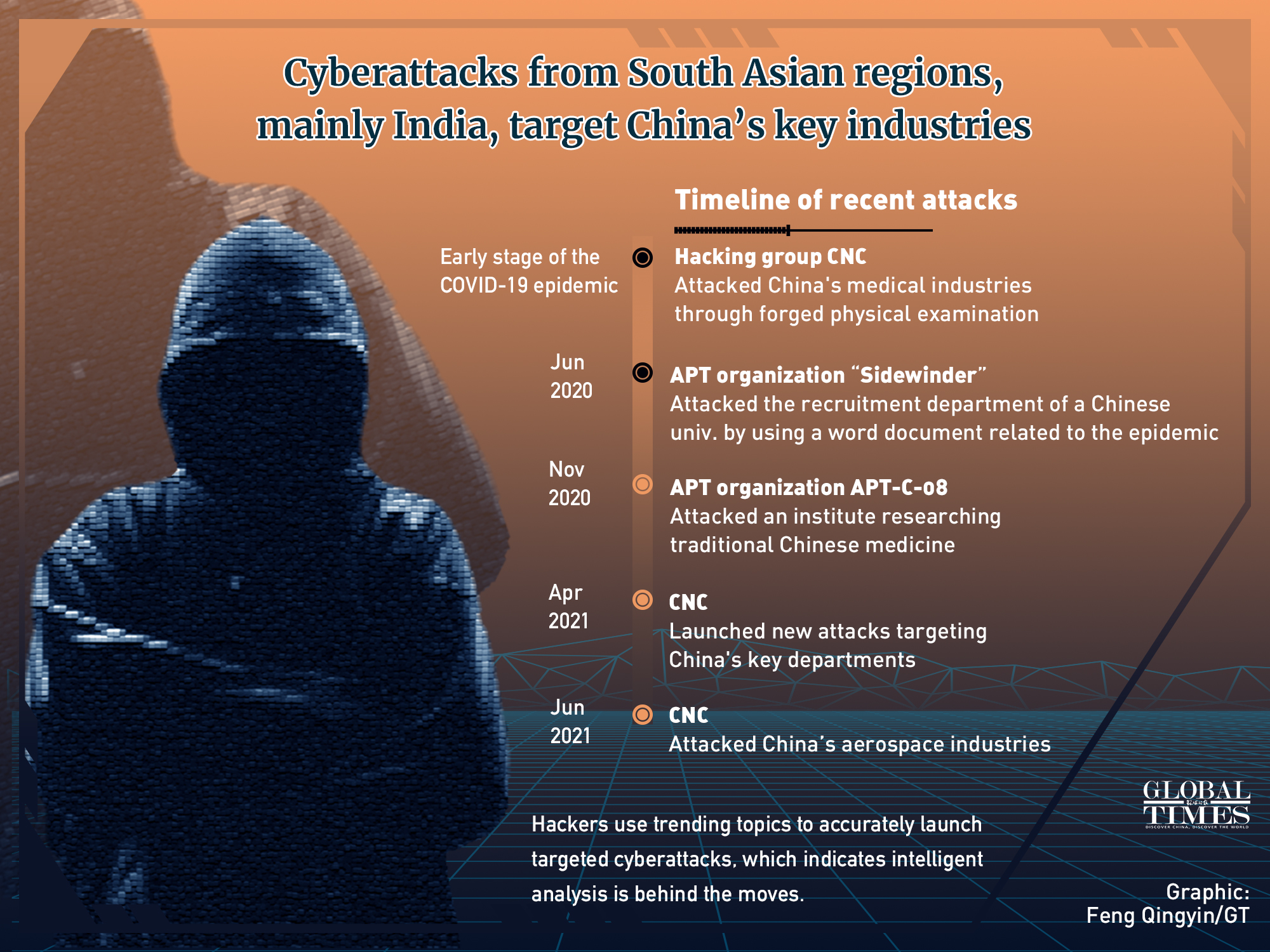
- Cybercriminals will exploit Pandemic-related weaknesses.
To bolster business resilience during the pandemic, organizations worldwide gained even more reliance on increasingly technological approaches. However, despite such efforts, threat actors have been able to leverage both human and technical weaknesses in more complex and widely distributed networks, causing significant damages to economic output and productivity.
Through 2022, threat actors will continue to exploit vulnerabilities that organizations will find difficult to fix due to ever-increasing complexity, allowing them to achieve their objectives. Other than notable and sensational exploits, 2022 is expected to be similar to 2021.
- Ransomware and other cyber threats will continue to increase.
As employees began working from home overnight, the IT industry faced a tumultuous period because they had to deal with massive increases in both scale and performance with little warning, and chaos is a favourite of hackers.
Within the next few months, a substantial number of work-from-home employees will be returning to the office – at least part-time – and IT security teams will quickly discover gaps in securing the enterprise network from the office. Cyberattacks are always more successful when there is network chaos.
- Automated endpoint security for enhanced security
The new remote workforce makes it an easy target for adversaries, so the idea of Extended Detection and Response (XDR) and Endpoint Detection and Response (EDR) solutions will entirely displace traditional anti-virus solutions concerning endpoint protection from advanced and sophisticated threats. Security information and event management (SIEM) is evolving into security automation and orchestration solutions that utilize artificial intelligence and machine learning concepts.
- Security framework embedded with work from anywhere will persist.
Companies adopt work-from-home policies in response to the pandemic, making cybersecurity a severe concern. Despite the objective of every organization to follow technological trends that enable anywhere, anytime access, they also have to consider the unprecedented increase in the attack surface across the entire network.
SASE, Cloud Access Security Broker (CASB), and secure web gateway (SWG) are just a few of the technologies that organizations will strategically invest in. By combining networking and security, these solutions and architecture allow consumers to gain direct, secure access to cloud-based apps while protecting users, programs, and infrastructure over distances.
- Cloud Workload Security
By multiplying the workload on cloud-based applications and deploying hybrid cloud strategies, organizations benefit from agility and scale while opening up new opportunities for adversaries to target vulnerabilities.
Cyberthreats will be a challenge for cloud workloads built on virtualized modules, like containers. The aim is to gain visibility and protect against threats by utilizing Cloud Workload Protection and Cloud Security Posture Management technologies. By integrating DevSecOps into CI/CD pipelines, these solutions will integrate infrastructure and application security while providing complete protection during that time.
- Security model based on zero-trust
Enterprises in India will adopt zero-trust architecture as one of the most critical security frameworks. To secure both users to the user, machine to machine, application to application, and user to application communication, organizations will implement zero-trust network access (ZTNA), micro-segmentation, and IoT security.
- Infrastructure security will be a significant issue across enterprise and service provider environments.
As cyberattacks increase and governments begin to recognize (finally) that critical infrastructure – and what enterprises deem “critical” to their businesses – is seriously at risk, infrastructure security will become increasingly important. It will take time for organizations to cope with today’s rapidly changing threat landscape, despite recent progress in India’s ranking on the Global Cybersecurity Index 2020. The government’s work on a National Cybersecurity Strategy is nearing completion.
Cybersecurity in 2022: What you need to know
To be prepared for any potential attacks, make sure to backup your system every few months.
Ransomware and phishing attacks are on the rise as digitization improves every industry. The purpose of ransomware is to encrypt and take control of vital data of a company or organization. Decrypting this data is only possible if a ransom is paid. The importance of the data at stake further accentuates the threat of ransomware, which impedes smooth functioning.

Private enterprises are not the only targets of cyber threats; government institutions are also at risk. In most cases, malware can easily encrypt the victim’s files after obtaining access to the operating system. In addition, modern encryption techniques are becoming increasingly sophisticated, which makes it extremely difficult to decrypt encrypted files.
Since the ransomware host has complete control over this key, the victim must pay a ransom in exchange for the key, allowing them to decrypt the information held hostage by the malware player. The losses incurred by such attacks are not limited to just the ransom amount but also include:
- The cost of repairing the compromised system.
- The interruption of business operations.
- The necessity of installing additional anti-malware software.
Here is some advice on how to protect yourself from the growing threat of ransomware as we head into 2022:
- A firewall setup that acts as a barrier between your system and external networks is an obvious option to have installed on your system. A firewall protects your sensitive information by preventing malware from entering via an external network.
- Updates and backups are performed frequently. Maintain your computer’s security by updating your operating system and anti-malware programs often. Updating your system regularly ensures that any security vulnerabilities will be covered and fixed.
- To be prepared for any attacks, it is a good idea to backup your system every couple of months. Additionally, ransom demand can be avoided if the data is stored in an alternative location. Before resuming work, it is imperative to ensure all malware has been removed.
- Cyber threats cannot be blocked by anti-virus software alone. Strengthen endpoint defence. To protect endpoint devices, organizations need to enable Endpoint Discovery and Response (EDR) solutions and other technologies.
- Zero Trust Security: Zero Trust is a security framework that ensures all users within your organization are authenticated and authorized to make security changes. Ransomware attacks are among the latest threats addressed by the program. By securing remote workers, constantly evolving hybrid cloud environments, and ransomware threats for securing infrastructure and data in an era of continuous innovation.
- Organizations face a massive increase in attack surfaces due to rapid digital transformation. Businesses must proactively assess their security posture to identify potential threats to their vulnerable assets because sophisticated cybercriminals are targeting the critical infrastructure of organizations. The cybersecurity ecosystem of organizations must also be revamped for mitigating potential risks and guaranteeing that the company’s operations run uninterrupted.
- It is advisable to use third-party email scanning or anti-phishing tools to identify and eliminate attempts of an attack and to mitigate the threat of phishing or social engineering attacks.
Cyber risk insurance is essential for businesses to counter the catastrophic effects of a cyber attack. Cyberattacks, which can cause business disruption, loss of revenue, and reputational damage, can prove costly and time-consuming without a comprehensive cyber policy. Besides developing a comprehensive cybersecurity roadmap, organizations should also create a business continuity plan and test their incident response procedures.
Cybercrime monitoring capabilities from Cyble, a cybersecurity services provider, enable clients to discover vulnerabilities in their digital footprints to help counter emerging cyber threats in their early stages.
In addition to providing organizations with actionable intel and a real-time view of the threat landscape, Cyble Vision’s core product, Cyble Vision, provides detailed analyses of data leaks, potential cyber threats, and malware. Cyble’s clients are notified ahead of time of potential hazards, not last-minute alerts. Data from the deep, dark, and surface web are captured and indexed, allowing Cyble to place a greater emphasis on actionable threat intelligence for its clients.
How to protect yourself from Cybercrime?
Cybercrime will inevitably occur! Viruses exist everywhere! Do you have any tips on avoiding malware, ransomware, and cybercrimes?

Due to the worldwide pandemic and remote working situation, Indian cyber frauds are on the rise and spreading like wildfire. At present, we must safeguard your secure data and keep our business competitive in the market.
Are being smarter than criminals should be the first step.
However, before we continue, let’s take a look at some facts:
- The files of 1 out of 5 businesses that paid the ransom were never recovered.
- Every 39 seconds, a company is attacked by ransomware.
Let’s take a closer look at the central point of this post now that we know how Cybercrime has become a threat.
In the online world, Cybercrime refers to threats, hacks, and malicious acts. Theft, security breaches, and financial exploitation are some common examples. Some other types of Cybercrime include cyberstalking, revenge porn, bullying, and harassment.
You can protect yourself from Cybercrime by following these steps:
- Strong Passwords
It is essential to have easy-to-remember passwords. Therefore, we choose special occasions that are easy to remember, such as birthdays and anniversaries. Unfortunately, this could put your device in danger and possibly jeopardize your finances.
It is recommended to use eight characters (including letters, numbers, and symbols) for all passwords.
Alternatively, you can use a password manager, which will assign and store unique, encrypted passwords for all your accounts. Once you log into the manager, the website’s password is applied. As the password isn’t stored on the website, a hacker will not access it.
- Ensure your software is up-to-date
Most cyber frauds gain access to your system by exploiting a flaw or exploiting an exploit. Update your software to fix these flaws, so they have less chance of gaining access to your information and personal data.
- Don’t fall for pop-ups
Emails and texts from scammers should be avoided!
Do not enter your username or password in an email or pop-up window. Visit the website directly from your browser, and Visit the website directly from your browser. You should never provide your login information to companies you are not familiar with via email.
- Use a VPN and a strong encryption password to protect your Internet network
An encryption password and virtual private network are good places to start. In addition to your devices, VPNs encrypt all traffic until it reaches its final destination. Cybercriminals will be unable to intercept anything but encrypted data if they hack your communication line.
When using a public Wi-Fi network, including in a library, hotel, airport, or café, make sure to use a VPN.
Keeping your software and apps safe online will reduce the possibility of Cybercrime. Using a VPN ensures you aren’t tracked and saves your internet traffic from being intercepted. Internet security makes it one of the best tools for the internet.
- Manage your social media settings
Keep your private and personal information locked up. It is never wise to post your confidential information publicly. A cybercriminal can easily access your data using social engineering, so sharing as little as possible is advisable.
Frequently asked security questions can be exposed if you reveal personal information, such as your maiden name or pet’s name.
- Protect yourself from identity threats
Whether you’re on the road or at home, identity theft can happen anywhere.
Cyber frauds have increased in India in recent years. Messages and emails containing personal information can lead to identity theft and financial loss if victims are tricked into giving away data through fraud or deception.
Therefore, securing your data is cr, and a VPN can protect your online data.
- Educate your children about internet risks
Parents’ concern about the internet has always existed.
Inform your children about internet scams and what internet usage is acceptable. If they face stalking, bullying, or online harassment, tell them they can come to you for help.
- Secure your computer and mobile devices
A firewall is the first line of defence in cyberspace – make sure it is activated. Various viruses and hackers can’t get into your system because it blocks connections to bogus or unknown sites.
Anti-virus/malware software is recommended. Install and update anti-virus software regularly to prevent viruses from infecting your computer.
It would help if you kept certain things in mind regarding mobile devices, such as installing the latest OS updates and maintaining your applications and operating systems updated.
- Protect your financial details
Please do not give your credit card details to a bank or company unless they specifically request it. Fraudsters often ask people to fill out random online forms with their details to steal their money or personal information.
- Protect your data
Files containing sensitive information, such as tax returns and financial records, should be encrypted. Moreover, make regular backups for your essential data and store it in another location.
- Understand what to do if you become a victim of Cybercrime
Last but not least, if you are a victim of Cybercrime, you need to inform your local police (in some cases, a Cyber Cell). The police need to be notified even if the crime does not seem severe. The following steps can be taken if you notice cybercriminals have stolen your identity:
- Fraudulent transactions should be reported to the banks and companies involved.
- Get your credit reports and place fraud alerts.
- Complain to the local police station or the Cyber Cell.




